What We Do
We don't copy and paste other organizations’ best practices.
We establish your requirements, targeted security posture and a means to maintain it through the TIGIR Methodology - an assembly of professionals, tools, comprehensive analysis. From these, we produce summarized, readable reports through patented algorithmic analysis that assesses and manages your organizational risks and threats to your assets.
We are committed to developing and instituting strategic security methodologies, frameworks and approaches that close the gap on your organization's exposure and vulnerabilities by identifying the right countermeasures and safeguards that ensure responsiveness to the speed of technological change.

Threat Classification, Profiling, Codification and Measurement
Threat Risk Assessment, Analysis and Mitigation Strategies
Cyber Security
Legislation and Threat Response
Strategic, Organizational, Programmatic, Technological and Administrative Responses
What We do
Security. We Do Security.
We don't do BandAids. We don't do tactics. We don’t do pie-in-the-sky. We develop strategic
approaches based on concrete assessments to ensure the highest
and most agile security posture possible. You won't find any sexy
terms or conflated promises here - we're serious about security
and we're focused on the problem, not low hanging-fruit.
HumanLed focuses on what countermeasures and safeguards you need to invest in to reduce
your risk - we're prescriptive and technology-agnostic. Our clients range from government,
private industry and federal and community law enforcement. The core of what we do is cyber
security but we assess all domains that play inextricable roles in iron-clad security - policy,
plication, physical, persec – when we develop your solutions.

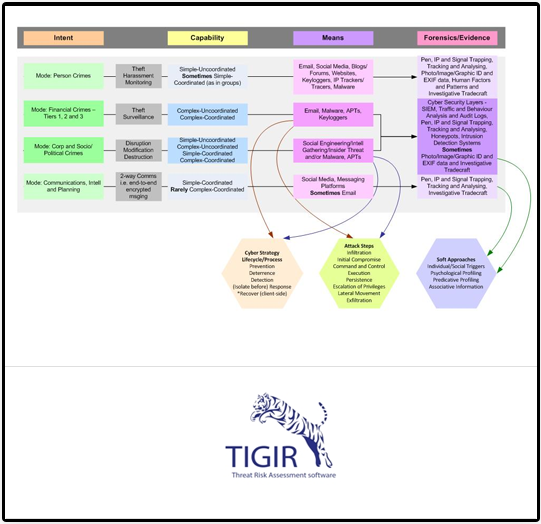
Framework
This is one of our more simple cyber assessment models
Improving an organization’s security posture, regardless of the threats or
malicious actors behind them, starts with thorough organization and asset valuation
before we scrutinize every important aspect of your organization to meet your security
targets. The methodology we use is our own - the Threat Information Gathering and
Incident Reporting (TIGIR) methodology - the basis of our patented Advanced Security
Intelligence Solution (ASIS), an Asset Threat and Risk Analysis tool called,
of course, TIGIR.
TIGIR is asset-driven to meet the new malicious and non-malicious threat
climate and to enhance the intelligence outputs and accurate valuation data, while
addressing gaps and vulnerabilities with prioritized recommendations.

